Last Updated: February 13, 2025
At Twing Data, we've built security and privacy into every aspect of our product and organization. Our approach combines deep expertise with robust processes to protect your metadata.
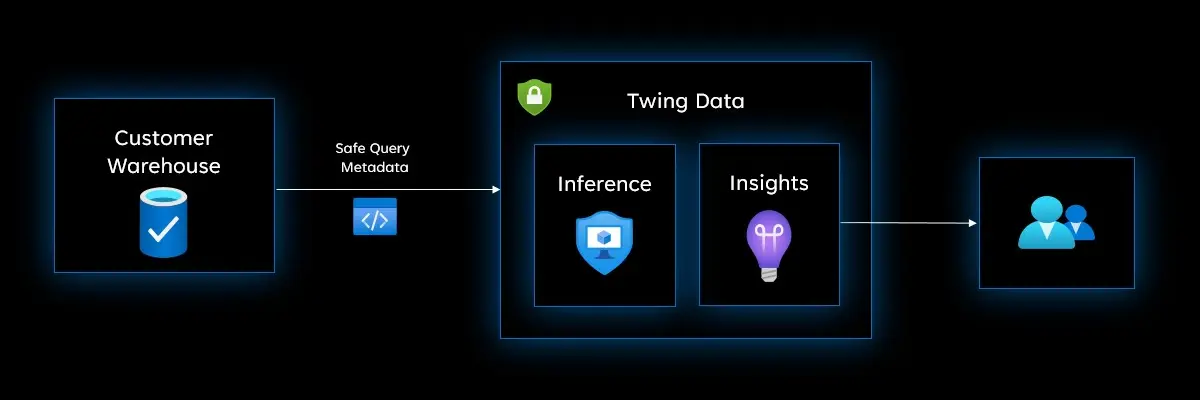
Twing Data operates with the principle of least privilege, requiring access only to your data warehouse metadata. This limited access approach means we avoid interacting with your actual data or sensitive information.
The metadata we analyze includes:
All metadata is securely stored in Twing Data's dedicated BigQuery account. We extract only the minimum subset of metadata required for our analysis and optimization services. Insights are generated and presented through our secure platform.
We maintain a strict security boundary that prevents access to any customer data stored in your data warehouse. We do not have read or write access to any of the customer's data that is stored in your data warehouse. This access is tightly controlled during the onboarding process where customers create a new user with a limited set of permissions.
The following is a diagram providing an overview of our system architecture. The key things to note are:
The Twing Data user facing application is deployed on fly.io. The metadata is stored in Google's BigQuery on top of Google's cloud infrastructure.
Glad you asked! If requested, we can redact the query text at ingestion time and replace it with a constant placeholder. This preserves the structure of the query text and allows us to analyze the pattern while removing any sensitive data.
Yes. We can provide you with an allowlist of IPs that will access your data warehouse. Please let us know during your onboarding process.
The user has only select permissions on the metadata database. This varies depending on the data warehouse. For more details, please refer to our integration docs.
We maintain a comprehensive incident response plan with defined SLAs. In the event of a security incident affecting your metadata, we will notify your designated security contact within 24 hours and provide regular updates until resolution.
We follow secure development lifecycle (SDLC) practices including code review requirements, automated security scanning, and regular penetration testing. All code changes go through multiple environments (development, staging, production) with appropriate approvals and testing at each stage.
Please contact us at security@twingdata.com.
Twing Data welcomes your questions or comments regarding this Security Policy. Please contact us at:
Twing Data, Inc.
169 Madison Ave STE 2815
New York, NY 10016
Email Address: security@twingdata.com
Telephone: (424) 229-2286